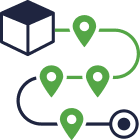
Our Zero Trust approach enables your mission goals and keeps the enterprise secure.
- Zero Trust takes cybersecurity to the next level and mitigates over 90% of cybersecurity risks.
- Monitoring, authentication and authorization are fundamental to our zero trust solutions.
Our cybersecurity services help protect everything from critical government assets to the infrastructure that you need to support your mission.
Cybersecurity Innovation
Effective cybersecurity includes proactive defense and effective incident management. Cyber Hygiene mitigates risks, manages incidents and ensures defensive systems work as intended.
- We deploy Cyber Hygiene strategies for consistent routines, multi-layered practices, and effective cybersecurity systems and tools.
- Our advisory, assessment and testing services evaluate your infrastructure, policies and practices to lower risk and resolve incidents.
- Collaboration on cybersecurity strategies is critical for operational effectiveness and mission success.
Analyst Recognition
#2 in Market Share by Revenue for Managed Security Services,
Worldwide - 2021
(June 2022)
Major Contender in IT Managed Security Services,
PEAK Matrix Assessment
(June 2021)